WordPress websites are often targeted by various hacking attempts, and one such prevalent attack is the WordPress Japanese Hack. In this blog post, we will delve into the details of this specific hacking technique, understand how it affects WordPress sites, explore the underlying causes, and provide you with preventive measures and recovery strategies. By staying informed and implementing the right security practices, you can protect your WordPress website from falling victim to the Japanese Hack.
The WordPress Japanese Hack Explained
How the Japanese Hack Works
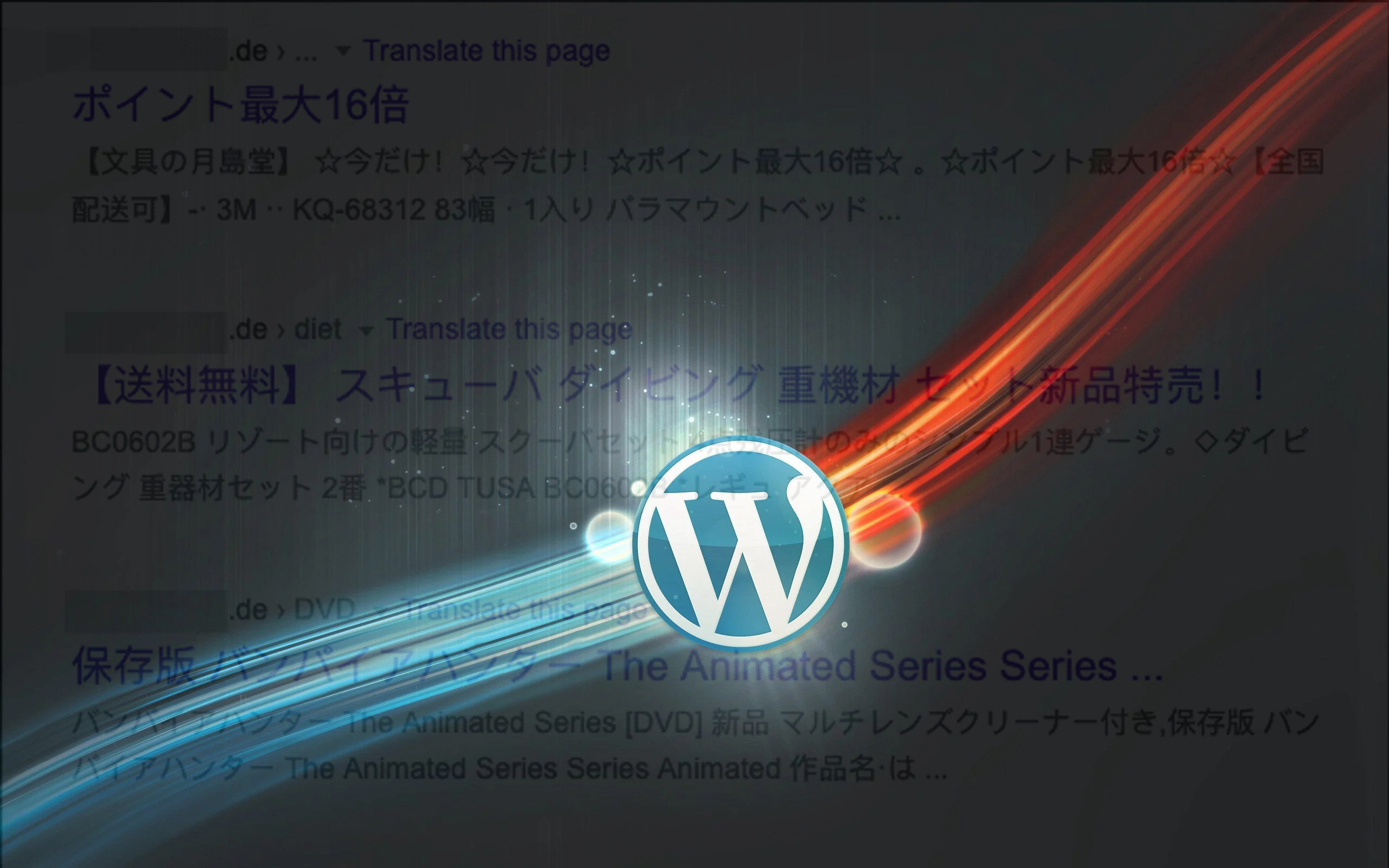
The WordPress Japanese Hack involves attackers injecting malicious code into vulnerable WordPress sites, which leads to the creation of spammy Japanese content on the affected pages. This content is usually hidden from regular website visitors but is indexed by search engines, damaging the website’s reputation and potentially affecting its search engine rankings.
The Japanese keywords hack is a notorious technique employed by hackers to inject autogenerated Japanese text into your website. These maliciously created pages are often tucked away in randomly generated directories. By leveraging this hack, hackers can manipulate your site’s settings, including geotargeting and sitemaps, to boost their own profits. If you receive a notification about an unfamiliar entity verifying your site in Search Console, it’s highly likely that your website has fallen victim to this hack.
To identify if your site has been compromised, begin by checking the Security Issues tool in Search Console. This tool will inform you if Google has detected any of these hacked pages on your site. Additionally, you can conduct a manual search by opening a Google Search window and typing “site:your site URL” (replace “your site URL” with the root level URL of your site). This search query will display the indexed pages, including any hacked pages. Take the time to browse through a few search result pages and watch out for any unusual URLs. If you don’t find any hacked content in Google Search, try using a different search engine with the same search terms.
When encountering a hacked page, you may experience a redirect to another site or come across a page filled with nonsensical content. In some cases, you might even encounter a message indicating that the page does not exist (such as a 404 error). However, don’t be deceived! Hackers often employ cloaking techniques to trick you into believing that the page has been resolved or removed. To detect cloaking, utilize the Inspect URL tool, where you can examine your site’s URLs and uncover any hidden content using the Fetch as Google feature.
If you identify any of these issues, it’s highly probable that your site has been impacted by this specific type of hack. Take immediate action to address the situation and safeguard your website’s integrity.
Causes and Vulnerabilities
Understanding the Entry Points
- Outdated WordPress Version: Running an outdated version of WordPress increases the vulnerability of your website. Hackers can exploit security flaws in older versions to gain unauthorized access.
- Vulnerable Themes and Plugins: Using outdated or poorly-coded themes and plugins can provide an entry point for hackers. These may have security vulnerabilities that can be exploited to inject malicious code.
- Weak Passwords: Weak or easily guessable passwords make it easier for hackers to gain access to your WordPress admin area and compromise your website’s security.
Preventive Measures Against the Japanese Hack
Strengthening Your Website’s Security
- Keep WordPress Updated: Regularly update your WordPress installation, themes, and plugins to the latest versions. This ensures that you have the latest security patches and fixes in place.
- Use Trusted Themes and Plugins: Only install themes and plugins from reputable sources and keep them updated. Remove any unused or outdated extensions to minimize potential vulnerabilities.
- Implement Strong Passwords: Use complex and unique passwords for all user accounts associated with your WordPress website. Consider using a password manager to generate and store secure passwords.
- Enable Two-Factor Authentication: Add an extra layer of security by implementing two-factor authentication. This adds an additional step for users to verify their identity, making it harder for hackers to gain unauthorized access.
Recovery and Cleanup
Steps to Restore Your Website’s Integrity
- Identify the Hack: Scan your website thoroughly using security plugins or online scanning tools to detect and remove the injected malicious code. Look for unusual files, code snippets, or Japanese content that you didn’t create.
- Restore from a Clean Backup: If you have a recent clean backup of your website, restore it to a previous version before the hack occurred. Ensure that the backup is free from any malicious code.
- Update Passwords: Change all passwords associated with your WordPress website, including admin accounts, FTP, and database access. This prevents the hackers from regaining access to your site.
- Harden Website Security: Implement additional security measures such as using a security plugin with a firewall, enabling web application firewalls (WAF), and employing real-time monitoring to detect and prevent future hacks.
While the WordPress Japanese Hack poses a threat to the security and integrity of your website, it is important to stay proactive in implementing preventive measures and promptly recovering from any successful attacks. By keeping your WordPress installation up to date, using trusted themes and plugins, employing strong passwords, and being vigilant about security practices, you can significantly reduce the risk of falling victim to the Japanese Hack. Regular monitoring and backup routines, coupled with a robust security strategy, will help safeguard your WordPress website against such hacking attempts.
Update on Google search console
When you’ve finished removing hacked files, check to see if your efforts were worthwhile. Remember those pages of nonsense you discovered earlier? Use the Fetch as Google tool to see whether they are still there. If they return “Not Found” in Fetch as Google, you’re probably in excellent condition and can move on to resolving the vulnerabilities on your site. You just need to wait and give Google time to recognize fixes!
Additional resources
If you’re still having trouble fixing your site, HIRE US TODAY!
These tools scan your site and may be able to find problematic content. Other than VirusTotal, Google doesn’t run or support them.
Virus Total, Aw-snap.info, Sucuri Site Check, Quttera: These are just some tools that may be able to scan your site for problematic content. Keep in mind that these scanners can’t guarantee that they will identify every type of problematic content.